
Phish2Pwn service by Oletros
The most common initial access to a company is Phishing.
And because phishing is so easy, espcially with generative AI and even more when you can spoof the company domain
93%
of security breaches involve Phishing
90%
of APT group use spear phishing
56%
of top 1k domains vulnerable to Domain Spoofing
Okay cool.. And so what?
You can't imagine how simple it is to exploit such misconfiguration.
Anyone with any mailbox can use your domain as legitimate sender.
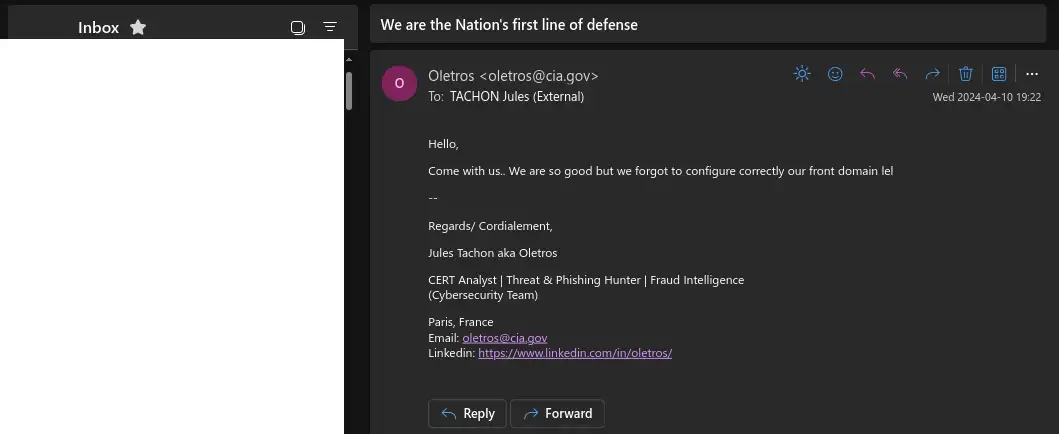 Sent from my offensive mail to my corporate email address.
Sent from my offensive mail to my corporate email address.CIA spoofed
Target sensitive collaborators
-
The targeting is easy. Go on Linkedin, search the company, find the people with sensitive roles, scrap Google, find the boss, and that's the classic attacker method
-
During years, the awareness of collaborators and people more generally were based on "look the sender" and with spoofing, the sender is the correct one.. Only by inspecting the source of the email, you can see the wolf
Create confidence in the target
-
Again the process is simple. Target people even if not customers, send them emails from official stores mail addresses, tell them for fake orders that they can cancel, ask their bank information for refund and that's it.
-
The problem for a company is, of course, the impact on its image, but also the responsibility that will be imputed to it. It exposes itself to the risk of being taken to court, because in a way it was this lack of security that enabled the fraud to be carried out so easily.
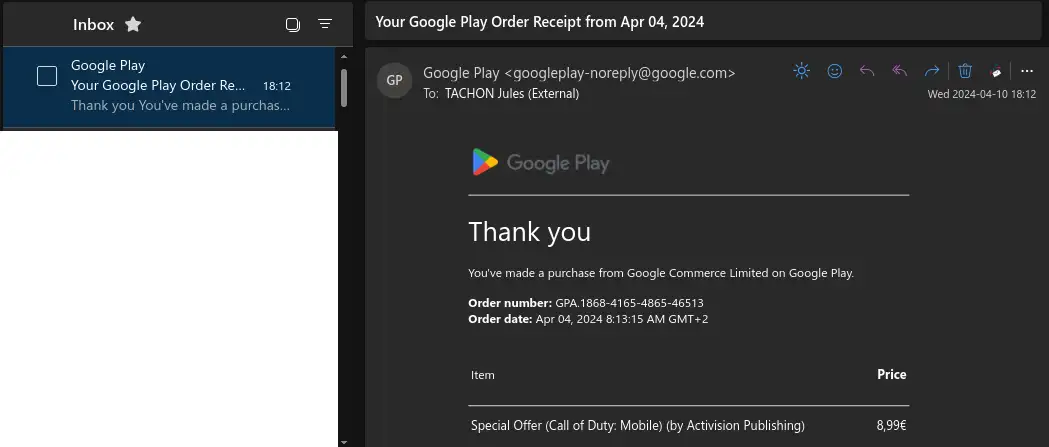 Sent from my offensive mail to my corporate email address.
Sent from my offensive mail to my corporate email address.Google spoofed
Questions & Answers
1. How to avoid being spoofed?
You need to create a strong policy regarding SPF, DKIM & DMARC technologies. You need to patch and monitor your domains DNS.
2. Why I sent that to you?
You can think that it's not my problem, and it's moved to do this but the truth is that so much people are impacted by your bad configurations because of the confidence that your brand inspires.
3. Why I do that?
-
Now you know me, and it's great if we do business in the future 😉
-
If we can stop the easiest phishing method of all time, it will be great
4. Why this name?
That's a great question.. I thought about it during a blackbox test against the infrastructure of one client and I knew I needed to create such projects
5. Open sourced the code?
It will be not a great idea as around 56% of the top 10k domains are vulnerable to domain spoofing. Don't want to make the blackhat life easier.
6. I don't understand. Can you help me?
Yes! If you have any questions, or requests, contact me on Linkedin or by email.

